So, when the talks starts rolling towards managing secrets and keys, one service of Azure you just cannot ignore is Azure KeyVault. You can keep all your secret parameters in this highly recommended HSM-protected managed vault and can securely use them from other services without the fear of those getting exposed. Great, you have implemented a fine level of security and a big round of applause 👏👏 in the room.
But.. ummm ...ok.. Now what about someone having access to the vault; intentionally (or accidentally may be a proper word) changes the value of any secret behind the scene without your knowledge. All the dependent downstream systems suddenly stops functioning and becomes unavailable straightaway. Isn't this qualifies for a security breach? Agree! 😔
I love a famous saying "It's not about the change but not having any knowledge of that change leads to road block". Let's take this as a thumb-rule and implement a notification system in place when someone adds/updates a secret in the KeyVault with a serverless approach throughout.
This article may also help you in your AZ-500 : Microsoft Azure Security Technologies preparation and lab. Let's dive! 👍
Prerequisites:
- Azure Subscription (Free subscription of 30 days will also do)
- SendGrid API Key (Follow this to create a free SendGrid account if you do not have it already and get the API Key)
- Basic knowledge of Azure services
We will use Azure Logic Apps along with Event Grid trigger to catch any KeyVault change event and would fire an instant email notification to the administrators.
- Login to Azure (If you do not have any subscription already then create one else login to your existing one)
- Create a resource group and then create a KeyVault in that resource group. Follow this link if you are new to KeyVault. Just create the vault and do not add any secrets now.
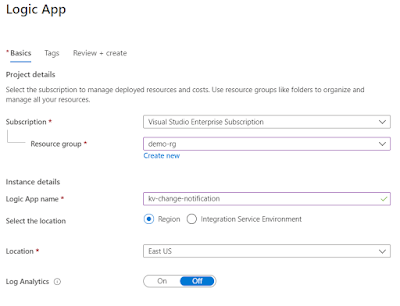
- Create an Azure Logic App (you can give any name of your choice; I have given kv-change-notification)
- Go to your Logic App and in the designer select the Event Grid trigger as below
- Select your tenant and hit Sign In. This will ask you for your Azure credential and will create your Event Grid connector.
- Click "Continue" to attach the event. Fill the details as required to connect with your KeyVault created earlier.
Resource Type as "Microsoft.KeyVault.vaults",
Resource Name is your KeyVault name (In my case I have give my vault name as MyVault0001),
Event Type Item - 1 as "Micsrosoft.KeyVault.SecretNewVersionCreated"
- Click "+ New Step" to choose the event to fire if the above step holds true. Search for SendGrid and select the send email action
- Provide a connection name and paste your SendGrid API . Hit Create. This will validate and would create your SendGrid connector.
- If the above validation is successful, the next window would ask you to provide all the mailing details. Fill it up as per the requirement. Make sure the From and To email addresses really exists.
- Hit Save at the top to save the logic app workflow. This is important.
Go to your KeyVault resource and enter a new secret.
Check your mail. Voila! You have new mail 📧
Now go ahead and modify the value of the secret in the vault and get notified once again. Great job!
So, with just few clicks you have developed a robust solution (that too serverless) which surely going to make the security admins very happy. Applause 👏 once again.
Congratulations! for coming this far. Hope this article will help you to further explore this feature.
Do share with me about your experience and what you have built upon this
foundation. You can take it up to any level and integrate. I would love
to hear from you.









No comments:
Post a Comment