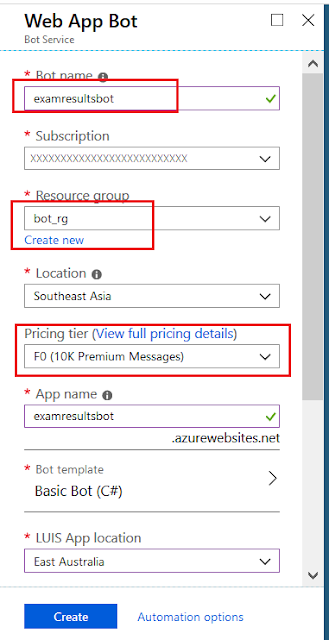
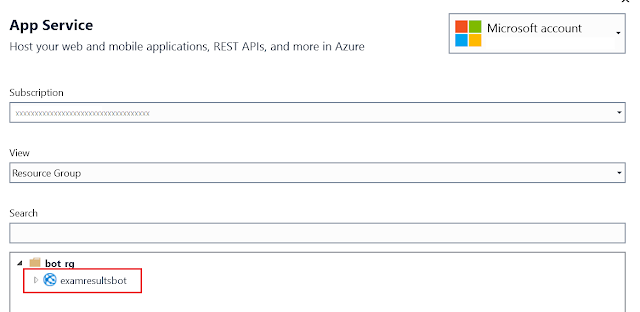
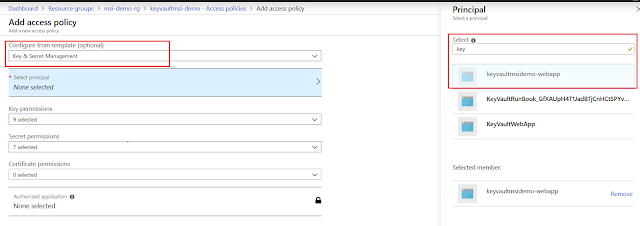
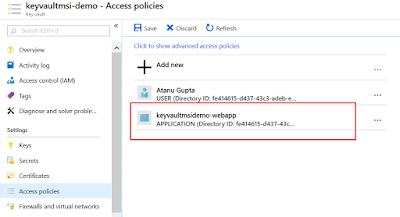
Let's simulate the security loophole
Web App (default).
Launch the endpoint of our web application.
Application Gateway
The same web endpoint now accessed through the API Gateway's public IP
Can you guess the security glitch here. Yes you are right. Your user has two endpoints now to access you application and so for the hackers 😈. They can easily bypass your gateway security gate and can directly access your application open for attacks.
So, what we are missing in our setup. A very important configuration. We need to make our website ONLY accessible via the gateway.
- Go to the Networking blade of your web application and click on "Configure Access Restrictions" under Access Restrictions
- By default you can see it allows access from any source. Click "+ Add"
- This is the important window. Here make sure you select "Virtual Network" as type, virtual network of your application gateway and its corresponding subnet. Here we are saying the web application to grant access only request coming from this VNET and not publicly. Click "Add Rule"
- Wait for few seconds. You can see now the public access is denied and the app gateway is only allowed. That's it.
Hit your web application endpoint. 403 Error. You have successfully restricted direct application endpoint access. Great.
Now hit the endpoint of your application gateway. No problem here, it's still serving our web application.
Good Job! You have successfully fixed a very important security glitch.
Congratulations. 👍👍
Congratulations. 👍👍